Currently, all eyes are on cyber security; but let’s not forget that physical security of one organization is equally important. Nevertheless, each organization needs to have proper safeguards in place to prevent a real threat and protect its employs and assets. Physical security refers to all actions taken in order to protect important data, confidential information, networks, software, equipment, facilities, company’s assets, and personnel.
External threats vary in accordance with the size, the importance and the activity area of each organization. Activists and opportunists, criminals or state sponsored organizations, even terrorists may act against an organization with the aim to create reputational damage, disruption of operations or profit loss.
In order to mitigate all the above-mentioned threats, facilities need physical access controls in place that monitor and manage access. Many mechanisms exist that enable control and isolation access privileges at facilities and are intended to discourage and detect access from unauthorized individuals.
How organization may be protected: 6 tips
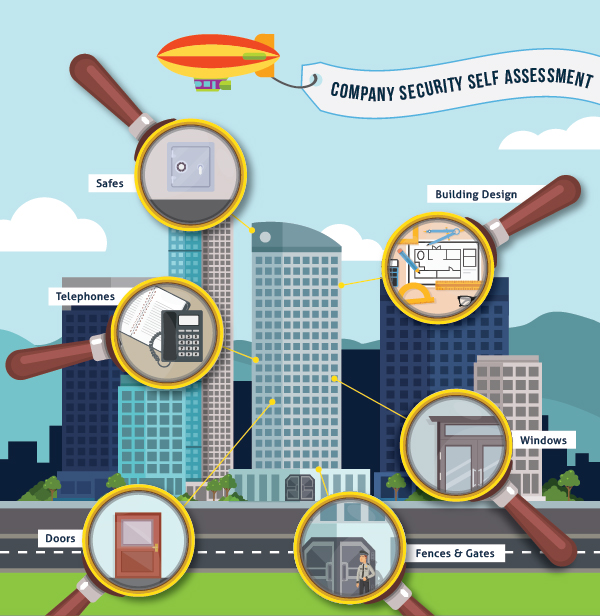
#1 Fences & Gates
It is important the building to be surrounded by an external fence with a gate from where arrival/departure of personnel should be checked. Venue should be secured during working hours and when the building is empty, as well. Only authorized personnel should be allowed to enter Company’s Facilities. Access control shall be performed from the main entrance through video monitor, access codes, badges or voice control. Company’s Management is responsible to change the access password and notify all personnel. Entering individuals should provide details about the reason of visit and the Company’s employee that is related to their attendance. ID checks should be performed to all incoming personnel who should also declare prior entering if they carry any dangerous asset or equipment. In case of supply providers and mail deliverers, an inspection should be performed to the delivered items.
#2 Doors
External doors leading from outdoor yards to the interiors should be strictly secured. Doors that are not used in office daily routine should be locked, keys should be retained by a responsible person and hand them over by request. During after office hours doors should be locked and the last person of each department that leaving department area is responsible for closing and securing doors and turning off lights.
#3 Windows
Bullet proof security windows should be locked during after office hours. It is important the windows to be free from promotional material so as to prevent visibility from outside. Alternatively, curtains (or blinds) should be installed on regular windows. Skylights should also be secured. External windows should be locked after completion of daily office hours. In case an employee wishes to use Company’s facilities and equipment after Office Hours, he/she is responsible for appropriate use of equipment and the final condition of windows.
#4 Telephones
Telephones should have a caller ID. When a threat is conducted via telephone call, the person who answers the phone call should under no circumstances transfer the line or put the caller on hold. Caller should not be interrupted, and the one who receives the call should be calm and courteous. Supervisor should be informed while caller is on the line, if possible. Persons who answer should act as they have difficulty hearing to keep the caller talking for as long as possible (tip: Ask questions, a pre-formatted set of questions to be available near main telephone answering stations )
#5 Building Design
Effective secure building design involves implementing countermeasures to detect, delay, and properly react to attacks from physical threats. Categorizing building sections should be restricted, private or public. Different access control levels are needed to restrict zones that each employee may enter depending on their role.
#6 Safes
Regarding the elements guarded in privacy (safes or cash desks), should be secured in areas where cannot be approached by the public and access should be limited or allowed to authorized persons only. It is useful in such places to install security cameras, motion detectors, alarms and fingerprint detection systems (where possible).