Vessel and facility operators use computers and cyber dependent technologies for navigation, communications, engineering, cargo, ballast, safety, environmental control, and for many other purposes. Emergency systems such as security monitoring, fire detection, and alarms increasingly rely on cyber technology and may be affected by attacks. As such, it is essential that companies prepare for a cyberattack and expeditiously address identified vulnerabilities both ashore and on-board ships.
Modern technologies can add vulnerabilities to the ships especially if there are insecure designs of networks and uncontrolled access to the internet. Additionally, shore side and onboard personnel may be unaware how some equipment producers maintain remote access to shipboard equipment and its network system. The risks of misunderstood, unknown, and uncoordinated remote access to an operating ship should be taken into consideration.
Cyber Risks detected onboard
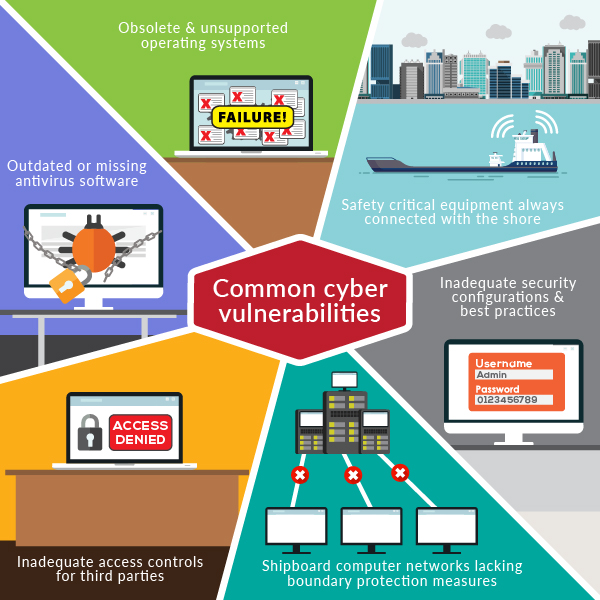
The following are common cyber vulnerabilities, which may be found onboard existing ships, and on some newbuild ships:
- obsolete and unsupported operating systems
- outdated or missing antivirus software and protection from malware
- inadequate security configurations and best practices, including ineffective network management, the use of default administrator accounts or passwords, and also ineffective network management which is not based on the principle of least privilege
- shipboard computer networks, which lack boundary protection measures and segmentation of networks
- safety critical equipment or systems always connected with the shore side
- inadequate access controls for third parties including contractors and service providers.
Procedural Control: 8 key elements
Some procedural controls are focused on how seafarers use the onboard systems, as listed below:
#1 Training and awareness
The internal cyber threat is considerable and should not be underestimated. Personnel, even with the best intentions, can be careless, so data can be mishandled, and files disposed of incorrectly. Training and awareness should be tailored to the appropriate levels for onboard personnel, including the master, officers, seafarers and shoreside personnel who support the management and operation of the ship.
#2 Upgrades and software maintenance
Hardware or software that is no longer supported by its producer or software developer will not receive updates to address potential vulnerabilities. For this reason, the use of hardware and software which is no longer supported should be carefully evaluated by the company as part of the cyber risk assessment.
*Note: Procedures for timely updating of software may need to be put in place taking into account the ship type, speed of internet connectivity, sea time, etc.
#3 Anti-virus and anti-malware tool updates
In order for scanning software tools to detect and deal with malware, they need to be updated. Procedural requirements should be established to ensure updates are distributed to ships on a timely basis and that all relevant computers onboard are updated.
Policy and procedures should be established for control over remote access to onboard IT and OT systems. Clear guidelines should establish who has permission to access, when they can access, and what they can access. Any procedures for remote access should include close co-ordination with the ship’s master and other key senior ship personnel. Systems should be monitored and reviewed periodically.
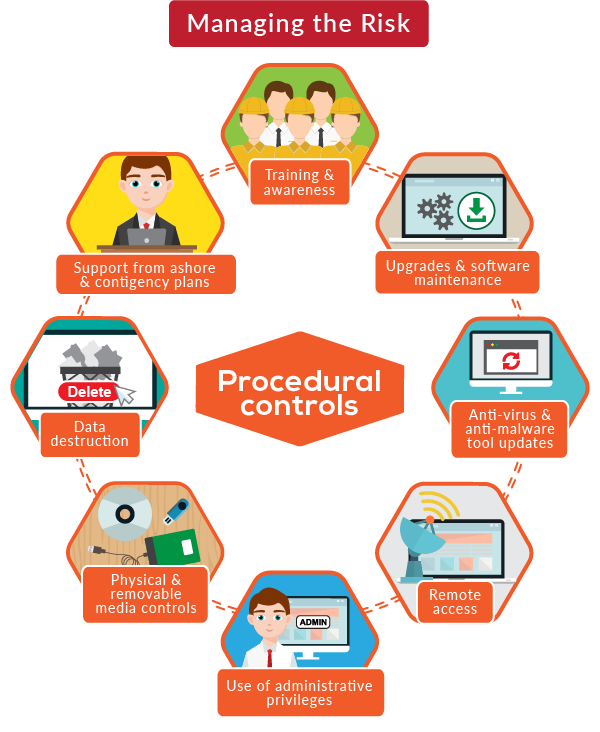
#5 Use of administrator privileges
Administrator privileges allow full access to system configuration settings and all data and should only be given to appropriately trained personnel who log into systems using such privileges. User accounts should be removed when they are no longer in use and should not be passed on from one user to the next using generic usernames. IT department is responsible for the monitoring and the privilege level of each employee.
#6 Physical and removable media controls
A clear policy for the use of such media devices is essential; it must ensure that media devices are not normally used to transfer information between un-controlled and controlled systems. In cases where it is unavoidable to use such media devices, for example during software maintenance, there should be a procedure in place to require checking of removable media for malware.
#7 Equipment disposal, including data destruction
Obsolete equipment can contain data which is commercially sensitive or confidential. The company should have a procedure in place to ensure that the data held in obsolete equipment is properly destroyed prior to disposing of the equipment thereby ensuring that vital information cannot be retrieved.
#8 Obtaining support from ashore and contingency plans
Ships should have access to technical support in the event of a cyber-attack. Details of this support and associated procedures should be available on board
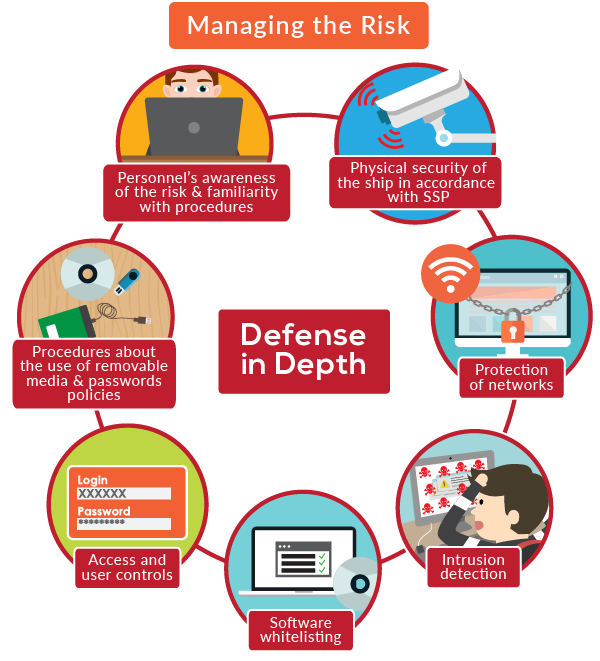
The ‘defence in depth’ approach
Vessel and facility operators should view cyber along with the physical, human factor, and other risks they already face. It is essential to protect critical systems and data with multiple layers of protection measures which take into account the role of personnel, procedures and technology. Defence in depth approach encourages a combination of physical security of the ship in accordance with SSP, protection of networks, intrusion detection, software whitelisting, access and user controls as also, the appropriate procedures regarding the use of removable media and password policies and, of course, personnel’s awareness.