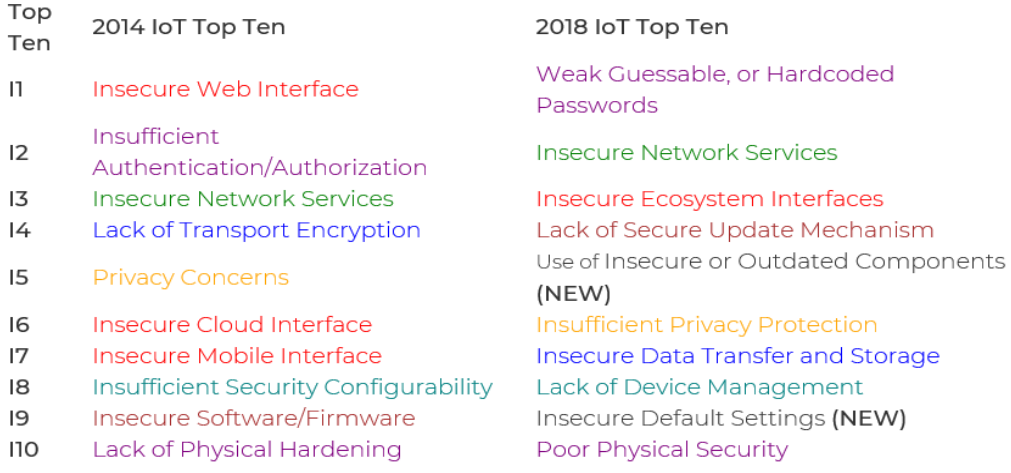
In its February 2020 newsletter the Korean Register informs that that the goal of the OpenWeb Application Security Project (OWASP)’s Things Internet Project is to help manufacturers, developers, and consumers further understand more accurately the security issues associated with the Internet of Things and further help users make wiser decisions in terms of security when building; distributing or evaluating IoT technology. Namely, in the infographic provided, OWASP informs about the ten vulnerabilities concerning the IoT.

Vulnerability 1: Easy passwords, inferred passwords or hardcoded passwords: OWASP informs that “using public authentication information or unchangeable authentication information that allows firmware or client software to be easily exposed to indiscriminate subpoena attacks, or to grant unauthorized access to distributed systems, including backdoors.”
Vulnerability 2: Insecure Network Services: “The unnecessary or unsafe networking service (especially the one exposed to the Internet) that undercuts the confidentiality, integrity/trust or availability of information or allows unauthorized remote control as it runs on the device itself.”
Vulnerability 3: Insecure Ecosystem Interface: “The unsafe web, back-end API, cloud or mobile interface of the device’s external ecosystem that allows for device or related components to be violated. Common problems include the absence of authentication/approval, the absence or weakness of encryption, and the absence of input/output filtering.”
Vulnerability 4: The absence of safe update mechanism: “The absence of a function to safely update your device. This includes a firmware verification member of the device, a member of a secure transmission method (not encrypted during transmission), a member of a rollback prevention mechanism, and a member of security change notification due to updates.”
Vulnerability 5: Use Unsafe or Out-of-Line Components: “Use software components/libraries that cause device infringement that are either unavailable or unsafe. This includes unsafe modifications of operating system platforms, and the use of thirdparty software or hardware components from the infringed supply chain.”
Vulnerability 6: Insufficient Privacy: “The user’s personal information is stored in the device or ecosystem and used unsafely, inappropriately, or without user permission.”
Vulnerability 7: Insecure Data Transfer and Storage: “The encryption or access control of sensitive data is not performed anywhere in the ecosystem, including storage, transmission or processing.”
Vulnerability 8: Absence of Device Management: “The absence of security support, including asset management, update management, safe disposal, system monitoring and response capabilities for devices deployed in production.”
Vulnerability 9: Unsafe default settings: “A device or system shipped in an unsafe default state, or a lack of function to more securely protect the system by restricting configuration modification by an operator.”
Vulnerability 10: The absence of physical protection: “No physical protection means, so potential attackers can acquire sensitive information to use for future remote attacks or take control of the device.”