Cybersecurity in the maritime industry is becoming increasingly crucial as vessels, ports, and supply chains embrace digitalization. With the integration of IoT (Internet of Things) devices, automation, and interconnected systems, the sector faces a growing threat landscape that includes risks such as data breaches, ransomware attacks, and sabotage attempts.
According to European Union Agency for cyber security, this shift is accompanied by a notable rise in cyberattacks targeting critical maritime infrastructure like ports and shipping firms, underscoring the necessity for enhanced focus and action on maritime cybersecurity.
The report utilizes the ENISA Cybersecurity Threat Landscape Methodology, analyzing a total of 98 publicly reported incidents during the specified timeframe. Data collection primarily focuses on EU member states and extends to global incidents impacting the EU. Major incidents were identified through open-source intelligence (OSINT) and cyber threat intelligence capabilities.
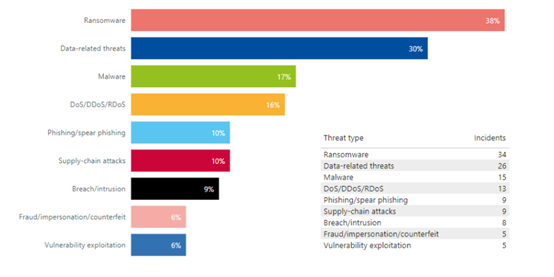
ENISA highlights that during the period of January 2021 to October 2022, the prime threats identified include:
- ransomware attacks (38%): a type of attack where threat actors take control of a target’s assets and demand a ransom in exchange for the return of the asset’s availability
- data related threats (30%): Sources of data are being targeted with the aim of unauthorised access and disclosure and manipulating data to interfere with the behaviour of systems.
- malware (17%): Malware is an overarching term used to describe any software or firmware intended to perform an unauthorized process that will have an adverse impact on the confidentiality, integrity or availability of a system.
- denial-of-service (DoS), distributed denial-of-service (DDoS) and ransom denial-of-service (RDoS) attacks (16%): Availability is the target of a plethora of threats and attacks, among which DDoS stands out. DDoS attacks target system and data availability and, though not a new threat, have a significant role in the cybersecurity threat landscape of the transport sector.
- phishing / spear phishing (10%): Social engineering encompasses a broad range of activities that attempt to exploit a human error or human behaviour with the objective of gaining access to information or services.
- supply-chain attacks (10%): A supply-chain attack targets the relationship between organisations and their suppliers.
During the reporting period, the threat actors with the biggest impact on the sector were state-sponsored actors, cybercriminals and hacktivists. We observed the following trends:
- Ransomware attacks became the prominent threat against the sector in 2022. Ransomware has been steadily increasing and the transport sector has been affected similarly to the other sectors.
- Cybercriminals are responsible for the majority of attacks on the transport sector (54%), and they target all subsectors.
- Threat actors will increasingly conduct ransomware attacks with not only monetary motivations.
- The increased hacktivist activity targeting the transport sector is likely to continue.
- The increasing rate of DDoS attacks targeting the transport sector is likely to continue.
- The main targets of DDoS attacks by hacktivists are European airports, railways and transport authorities.
- During this reporting period, we did not receive reliable information on a cyberattack affecting the safety of transport.
- The majority of attacks on the transport sector target information technology (IT) systems. Operational disruptions can occur as a consequence of these attacks, but the operational technology (OT) systems are rarely being targeted.
- Ransomware groups will likely target and disrupt OT operations in the foreseeable future.
According to the report, in 2022, ransomware attacks emerged as the primary threat to the sector, surpassing the data-related threats that dominated in 2021. Nevertheless, ransomware groups are still seen as opportunistic and not specifically targeting the transport sector more than others. Recent trends suggest no notable increase in ransomware attacks targeting transportation compared to other sectors. Ransomware incidents have been on the rise overall, affecting the transport sector in line with other industries.
Key challenges to manage cyber security
According to DNV, effectively managing cybersecurity in the dynamic and intricate energy sector is far from simple. The sector is experiencing significant digitalization, innovation, and shifts toward cleaner energy sources amid changing global demand and the impacts of conflict in Europe, which are influencing global energy prices and distribution patterns.
#1 The ‘wait and see’ effect is holding back progress: Six in 10 C-suite respondents acknowledge, for example, that their organization is more vulnerable to attack than ever before, but far fewer (44%) expect to make urgent improvements in the next few years to prevent an attack.
#2 The air gap is closing fast: When considering the risk of a cyber-attack on their industrial control systems, energy businesses have taken some comfort from the knowledge that their OT platforms have traditionally had an ‘air gap’ insulating them from the IT network.
#3 A global shortage of expertise: In an unfolding cyber incident, where hackers have infiltrated the network and need to be contained, every second counts. It’s therefore concerning that just 31% of respondents assert confidently that they know exactly what to do if they became concerned about a potential cyber risk or unfolding attack.
#4 Complex supply chains disguise critical vulnerabilities: Supply chains in the energy sector are global in scale and increasingly complex, relying on third and fourth parties whose cyber security systems and processes are harder to assess with certainty. Consequently, cyber security across the supply chain is an area in hich respondents are less confident than they need to be to protect their critical systems and data.
Where we stand
The issuance of the Navigation and Vessel Inspection Circular (NVIC) by the US Coast Guard (USCG) in March 2024 underscores the critical importance of cybersecurity in the maritime sector. With cyber incidents such as ransomware attacks, data breaches, and IT disruptions becoming the primary concern for companies globally, as highlighted in the Allianz Risk Barometer 2024, the maritime industry is not immune to these threats.
As the maritime sector increasingly relies on digital technologies for navigation, communication, and operational efficiency, it becomes more vulnerable to cyber threats. A breach in cybersecurity could not only disrupt operations but also compromise the safety and security of vessels, crew, and cargo.
Moreover, in the broader context outlined in the Global Risks Report, rapid technological change presents both opportunities and challenges. While advancements in technology enhance efficiency and connectivity, they also introduce new vulnerabilities and risks. Economic uncertainty, exacerbated by factors such as geopolitical tensions and climate change, further complicates the landscape.
In conclusion, the transport sector faces an evolving cyber threat landscape characterized by ransomware’s increasing prominence and hacktivists’ use of DDoS attacks for geopolitical motives. As cyber threats become more complex and targeted, proactive cybersecurity measures and collaboration between transport stakeholders and cybersecurity professionals are imperative to mitigate risks and ensure the resilience of critical transportation infrastructure.

































































