Cyber threat is any event or incident that aims to impact organisational operations, such as mission, functions, image, or reputation, organisational assets, individuals, other organisations, or the Nation through an information system. This is achieved through unauthorised access, destruction, disclosure, modification of information, and/or denial of service.
Mainly, cyber threats should be categorised in order to better understand the vulnerabilities of assets.
According to KR Guidance for the maritime cyber security system requirement, external environmental factors of internal information technology and operational technology should be identified and categorised as threats.
Moreover, the Open Web Application Security Project (OWASP) is an open source web application security problem that focuses on the research of web exposure, malicious files and scripts, security vulnerabilities.
OWASP Top 10 are published in 2004, 2007, 2010, 2013 and 2017.
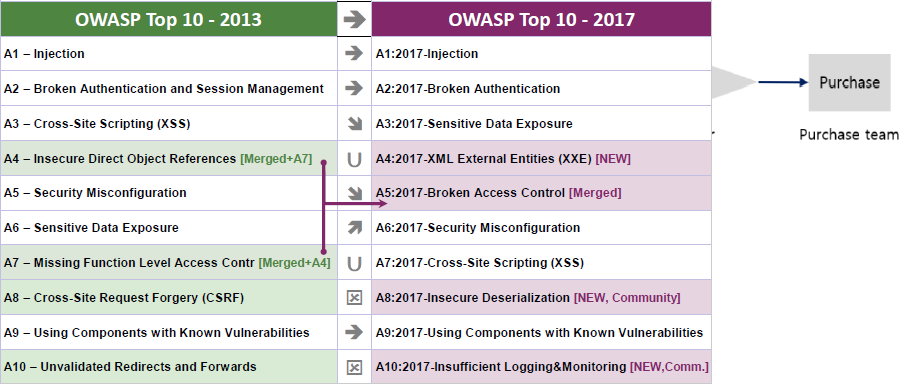
Injection is a vulnerability that takes place when an attacker identifies and executes maliciously injected data as part of a normal query of the data base in a web application.
Injection attacks are easy-to-happen; data is in put or database information is requested.
The injection consists of four different types:
- SQL injection;
- HTML injection;
- OS command injection;
- LDAP.
Also, there are various types of injection depending on the attack method and language used.
Specifically, Structured Query Language (SQL) injection is a practice used to adjust or retrieve data in a SQL database.
When a cyber attacker executes specific SQL actions, an unauthorized user can change existing data, modify transactions and balances, and retrieve and/or destroy all server data.
The most crucial form of SQL injection is that the attacker gets root access to the machine and give it full control.
Finally, preventing injection requires keeping data separate from commands and queries:
- It is preferable to use a safe API, to prevent the use of the interpreter entirely or provide a parameterized interface or migrate to use Object Relational Mapping Tools (ORMs);
- The use of positive server-side input validation is ideal;
- Use LIMIT and other SQL control within queries to prevent mass disclosure of records in case of SQL injection.






























































