Considering shipping’s digitalization era, a common issue that owners and operators are dealing with is cyber security crime, which certainly poses a major risk for companies’ software value. However, it is proved that the more knowledge companies have, the better decision they can make, in response to those malicious activities.
As a matter of fact, cyber security is not only a maritime problem, as every business and every individual can be subject to such crime.
Although, during the unprecedented crisis of COVID-19, it was noticed that cyber-criminal activities were increased, exploiting the vulnerability of users working from home.
Following the situation, Nautical Institute’s Cyber Security webinar hosted by David Patraiko, FNI Director of projects, focused on how shipping can stay protected against cyber-attacks.
One thing is for sure. Cyber-crime is a massive business, since all hackers are very well-organized, and they put a lot of time and effort before launching a cyber-attack.

According to some statistics issued by Juniper Research analysts, cybercrime-related costs reached to US$2 trillion during 2019.
As we are all online, criminals see this as an easy way to make money, while they aren’t often punished.
…Mr. Colin Gillespie, Director (Loss Prevention) at the North P&I Club, noted.
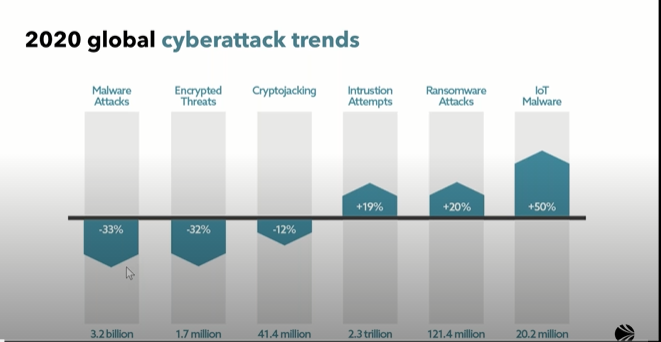
Among others, the current cyberattack trends observed are the following: malware attacks, encrypted threats, crypto jacking, intrusion attempts, ransomware attacks and IoT malware.
Due to the rapid digitalization of maritime industry and coronavirus pandemic which forces employees working remotely, companies are more exposed to cyber incidents than ever.
Although, someone might wonder what shipping players should be doing in order to name themselves as cyber-secured?
As Mr. Colin Gillespie explained, owners and operators should take into consideration:
- Identify threats
- Identify vulnerabilities
- Assess risk exposure
- Develop protection and detention measures
- Establish contingency plans
- Respond to and recover from cyber security incidents
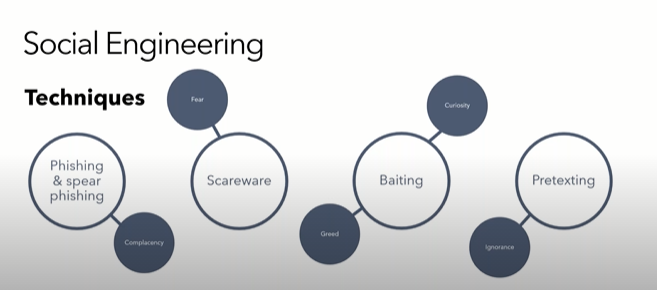
What is more, it is observed that malicious actors begin to use several techniques so as to get through someone’s system. Therefore, companies need to be aware and suspicious of:
Phishing and Spear phishing
It can be an email or a text message telling you you’re about to receive some money, but you just need to provide some personal details first.
Some hackers may try to get you to click on a link that could lead to a website that downloads malware or a fake site that contains advertisements and trackers.
Scareware
You may receive an email reporting that your software system has been infected, when it actually hasn’t.
By creating fear and anxiety, cyber hackers manipulate users and make them believe they need to download or even buy malicious software for their system’s protection.
Baiting
Baiting techniques often distributes malware-infected devices to employees.
Consequently, hackers rely that this hardware will be inserted into network-connected computers, giving them the opportunity to spread malicious code.
Pretexting
In this form, the attacker tries to convince the victim to share valuable information or access to a system.
In fact, the hacker pretends to be someone in power and persuade the victim that the scenario is true in order to collect vital information.

































































