The lack or even absence of a system operation security policies can result to cyber crimes. When an unnecessary or vulnerable service is activated there is a possibility that it could be detected through network scanning and an unauthorized access or malicious code distribution will be exploited to hack the service.
For instance, KR refers to a Server Message Block (SMB) protocol used to exploit a vulnerability that could bypass the network traffic to an SMB server. This allows hackers to steal the corresponding login information of Windows PC users.
In light of the cyber threats, KR provides guidance for maritime cyber security system requirement:
- Operating system interface restriction (231.1): It should be ensured whether unauthorized interfaces, ports or services exist in the operating system;
- Change security setting (213.3): When introducing information assets, the default value should be newly set or changed according to the security policy or change management standard of the company;
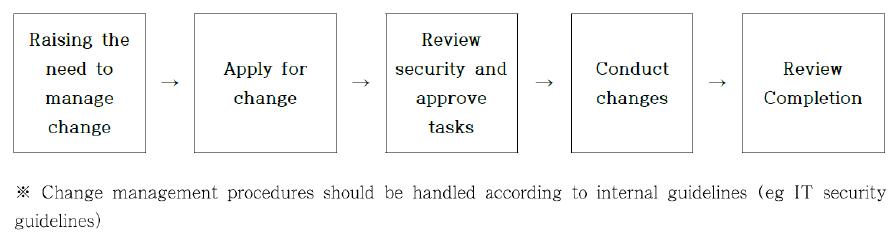
- Change management (213.4): Prior to changing the system, the relevant data should be backed up and saved in the possibility of a system failure;
- Prevent auto-execution (213.6): All software accessing information assets should be configured to nor run automatically;
- Performing change management (213.7): When performing change management, pre-test should be conducted and change management records should be kept and managed.