In response to the cyber security matters that keep arising, US Coast Guard has released Navigation and Vessel Inspection Circular (NVIC) 01-20, in which addresses cyber security risks and states its position on cyber risk management controls for maritime facilities regulated under the 33 CFR 105 code of federal regulations.
Following the current COVID-19 outbreak, it was noticed that cyber-criminal activities were increased, exploiting the vulnerability of users working from home.
Specifically, amid this unprecedent crisis, malicious actors are looking to steal critical data from someone’s work.
There are many real-world cyber incidents occurred within the shipping industry. Cyber-attacks have no borders, and everyone can get affected.
…said Captain Dave Nichols, USCG (ret.) is Business Development Director for Marine and Offshore at ABS Group.
Considering the situation, speakers at the ABS “Understanding Cyber Security Through the Lens of USCG NVIC 01-20″ webinar, Captain Dave Nichols (USCG, ret.) and Cyber Security Assessor Brian Shajari, discussed how to navigate NVIC 01-20 and highlighted some of the phishing activities that are increasingly utilized due to the pandemic:
- Phone Scams
- E-mails claiming to be governments’ announcements
- Online meeting hijacking
- Financial theft
Despite the coronavirus threats that are observed, there are several security challenges that shipping industry ignores, which are the following:
Lack of reporting: Many facilities believe that if they report a cyber-attack, this info will be further released to the public and the media may damage their reputation.
Not assessing vulnerabilities: A lot of facilities don’t assess their cyber vulnerabilities and their cyber security issues.
Not involving management: Shipping hasn’t realized yet the importance of getting a managed maintenance plan involved in their cyber security programs.
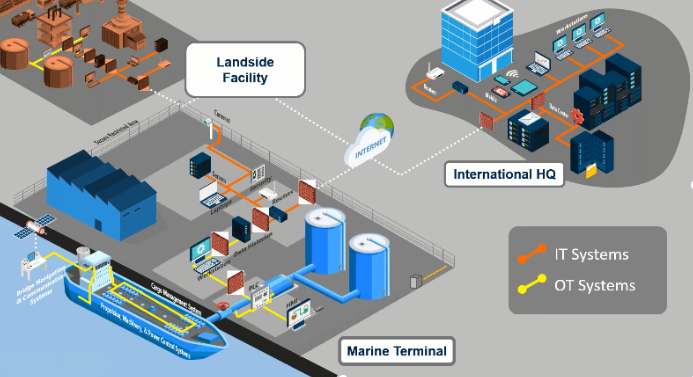
With facilities being connected to terminals or headquarters, doing business via the internet and their systems communicating even in another country, there is a worldwide exposure over the internet which can result to a cyber-attack.
IT systems move data and connect with other operational technology systems, so that devices can communicate with each other. Although shipping must consider that if somebody access their operational technology systems, this can easily lead to a major safety incident.
In light of the above, USCG NVCI 01-20 makes it clear that the Facility Security Officer (FSO) is responsible for the cyber security matters, but that doesn’t mean that they must be cyber security experts.
FSOs must know and understand cyber risks and how vulnerabilities are created. They really need to introduce cyber security into their assessments. In fact, cyber assessments should be treated the same way as the physical security ones.
…as Cyber Security Assessor Brian Shajari, mentioned.
In a Cyber Facility Security Assessment, it is recommended participation by the above stakeholders:
- FSO
- AFSO
- IT
- OT
- Operations staff
- Management team
- HSSE/She Manager
What is more, operators should not involve cyber security in their Facility Security Plan (FSP), as it is suggested to create a cyber security guidance or annex in which will include every vulnerability observed, a prepared incident plan and the use Incident Command System (ICS) for cyber response.
Concluding, according to USCG, performing cyber security assessments and addressing cyber security will be a requirement. Although its implementation is not required until 30 September 2021, operators may benefit from an early adoption, as they can:
- Preserve their facilities’ reputation
- Foster safety into their cyber program
- Be prepared to exceed the expected standards outlined in the USCG NVIC 01-20
- Reduce the likelihood of a cyber attack
Implementing Cyber Risk Management will put you in a better position to be more competitive.




























































